NOTE: This is a summary of a paper presented at the Institute of Navigation’s International Technical Meeting in January 2021. Register to watch the session.
It was once considered an esoteric and theoretical type of cyberattack, seen only in James Bond films and academic papers. But radio frequency (RF) location spoofing is now causing real concern for users of GPS and GNSS receivers.
The recent emergence of software-defined radios has made spoofing much easier to carry out. By broadcasting a fake GNSS signal at a higher power than the genuine signal, an attacker can force a receiver to lock on to the fake signal and miscalculate its own position. That can have a wide range of consequences, from steering off course to outputting a false timestamp.
Real-world spoofing attacks are of growing concern
Recent real-world events have shown that spoofing is a genuine threat to unprotected receivers. In 2017, a mass spoofing attack in the Black Sea disrupted the navigation systems of at least 130 ships, causing them to report a position at an inland airport. And in 2019, GPS positions reported by ships moored in the port of Shanghai showed the vessels mysteriously sailing in circles.
As more of our critical infrastructure – from energy grids to telecoms networks – uses GNSS for position, navigation and timing (PNT), governments are increasingly concerned about such interference. In December, the US Department of Homeland Security published its Resilient PNT Conformance Framework to help receiver developers and integrators design robust systems that can detect and reject and/or recover from attacks.
Earlier Spirent lab tests revealed receiver vulnerability to spoofing
A key part of our work at Spirent is helping receiver designers and developers to understand the threats posed by malicious disruption to GNSS signals, of which spoofing is a particularly worrying example.
Last year at the 2020 ION GNSS+ virtual conference, we presented the results of tests conducted in our labs, which showed that all three of the commercially available GPS receivers we tested were vulnerable to spoofing. The test was written up in Inside GNSS and was chosen by the editor as one of the 12 most important stories of 2020.
As important as those tests were, they were undertaken in the lab using a Spirent simulator to generate both the real-world GPS signals and the spoofed signals. With none of the noise and variability of the live environment, they represented a ‘worst case’ scenario, which receivers are unlikely to experience in the field. Generating both sets of signals from the same simulator also meant they were perfectly correlated, something a spoofer would find very challenging.
New tests were carried out in a more realistic live sky environment
Given that real-world spoofing attacks would not take place under lab conditions, we wanted to determine how effective an identical spoofing attack might be in the live sky environment.
We conducted a new set of tests using a static roof-mounted GPS antenna to feed the live signal into the laboratory, and a Spirent GSS7000 simulator to generate the replica signals (see graphic). Both sets of signals were played to the (static) receivers under test via coaxial cable.
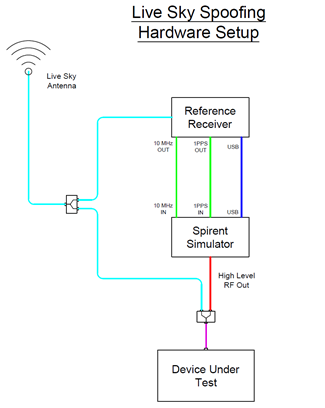
Test set-up for authentic live sky spoofing: a Spirent GSS7000 simulator with Standpoint tool and reference receiver provides timing and ephemeris data from live sky and reference signals for synchronisation.
It’s important to note that as these tests took place during the COVID-19 lockdown, they were conducted at an urban home location rather than in Spirent’s Paignton lab. However, the parameters and simulator equipment we used were the same, and we were able to test two of the three commercial GPS receiver models that we’d previously tested in the lab.
As previously, we tested the impact of the spoofing attack by having the receivers initially lock on to the live signal, and then ramping up the power levels of the replica signal to determine the power at which it would start to have an impact (if it had an impact at all). We also re-ran the tests with the simulated spoofer at distances of 10m, 50m and 100m from the receiver, to understand the impact of distance on spoofing effectiveness.
Test results confirm receiver vulnerabilities, with some differences from the lab results
Given the dynamic nature of the live sky environment, and possible multipath effects at the antenna location, we expected to see more unpredictability in the results than in the lab-based tests. With the spoofer at 10m distance, the reported ground tracks of the two receivers supported that expectation. In the lab, both receivers were successfully spoofed into reporting the false position. In the live sky test, however, only Rx2 (in purple) reports a position close to the spoofer, with Rx1’s position (in green) wandering around the truth location.
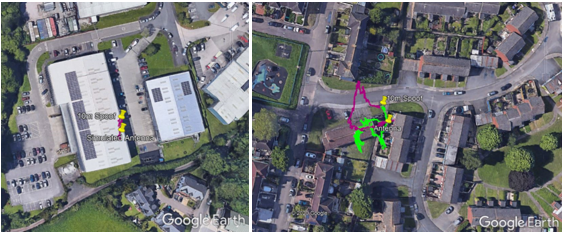
Reported ground tracks of Rx1 and Rx2 during the 10m test case. Left: 10m Simulated; Right: 10m Live Sky
With the spoofing signal moved further away, to 50m and then 100m, both receivers were successfully spoofed to the false location co-ordinates – albeit with more erratic paths than we saw in the lab.
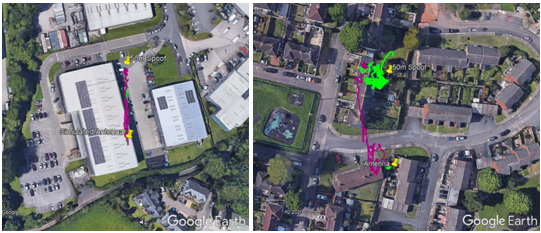
Reported ground tracks of Rx1 and Rx2 during the 50m test cases. Left: 50m Simulated; Right: 50m Live Sky
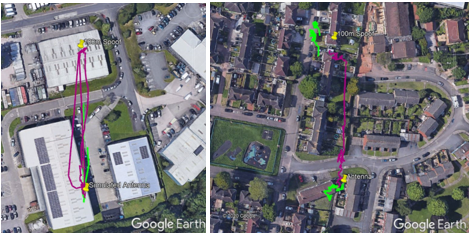
Reported ground tracks of Rx1 and Rx2 during the 100m test cases. Left: 100m Simulated; Right: 100m Live Sky
These tests confirm that even in more dynamic and unpredictable live sky environments, the two receivers we tested were vulnerable to spoofing attacks within a 50–100m range of the spoofer. In addition to the reported ground paths mapped above, an examination of the pseudorange residuals reveals the full extent of the impact on the receiver – which is explained in depth in my ION Technical Meeting session and accompanying paper: An Assessment of the Difficulties Spoofing Live Sky vs Simulated GNSS Signals (ION registration required to download).
Future tests will cover additional locations and antenna types
While the live sky tests have the disadvantages of not being truly repeatable and of only being applicable for a single location, the similarities with the results obtained in the lab lead us to conclude that spoofing is a real-world threat to unprotected receivers, especially single-constellation, single-frequency commercial receivers like the ones tested.
Given the more realistic environment of the live sky tests, we recommend that receiver developers use a live sky feed to assess the robustness of the receiver in the face of attack, and lab simulation to determine the likely consequences of an attack.
When COVID-19 restrictions are lifted, we hope to be able to conduct further live sky tests in different locations around the globe, including dense urban locations with high degrees of multipath. We also hope to repeat the tests with a wider array of receiver antenna types, to establish the importance of antenna performance in the outcome of spoofing attacks.
Want to learn more about spoofing and how to mitigate the potential impact of an attack? Download our GNSS Signal Spoofing white paper.






